Why PII Guardrails Matter for Your AI Applications
- Regulatory Compliance: Meet requirements for GDPR, CCPA, HIPAA, and other data protection regulations
- Data Breach Prevention: Stop sensitive information from leaking through AI responses
- Customer Trust: Demonstrate commitment to privacy and data protection
- Cost Optimization: Avoid regulatory fines and reputational damage
- Operational Excellence: Automate PII detection and redaction at scale
Overview of Portkey’s PII Protection Options
Portkey offers multiple approaches to PII protection:1. Portkey Native PII Detection
- Comprehensive PII detection using advanced ML models
- Detects and redacts: names, emails, phones, addresses, SSNs, credit cards, IP addresses
- Simple configuration with immediate results
- Available on Production and Enterprise plans
2. AWS Bedrock Guardrails Integration
- Enterprise-grade PII detection from AWS
- Supports custom PII patterns via regex
- Currently focuses on SSN redaction by default
Learn about AWS Bedrock Guardrails
3. Partner PII Solutions
Pangea
Advanced PII detection and redaction
Patronus AI
Enterprise PII for business documents
Azure PII
Microsoft’s PII detection service
How PII Transformation Works
When PII is detected in a request, Portkey transforms it before sending to the LLM: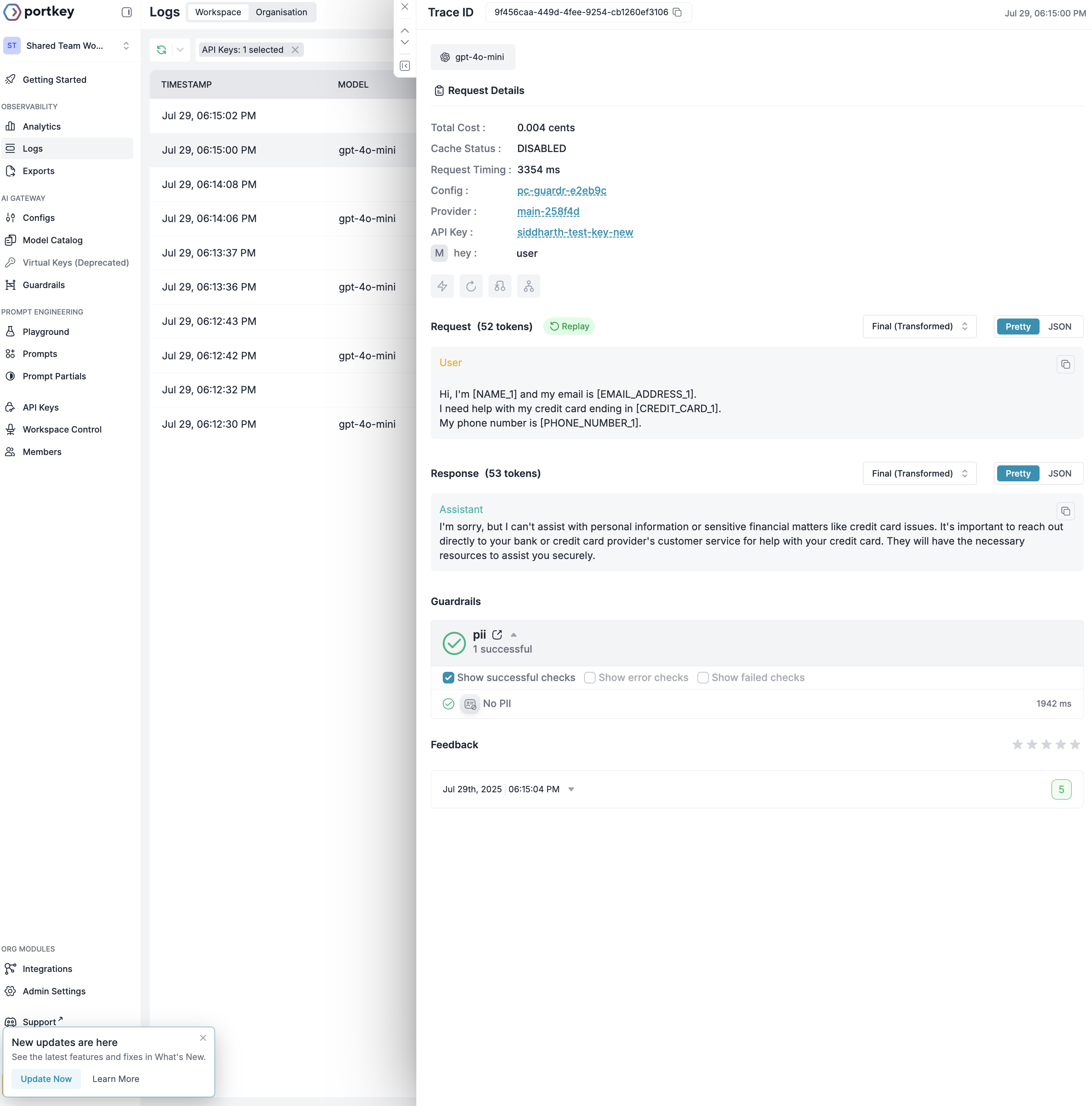
- Original: Contains actual PII like names, emails, SSNs
- Final (Transformed): PII replaced with numbered placeholders
- Status: Shows if transformation occurred
Setting Up Portkey’s Native PII Detection
Step 1: Create a PII Detection Guardrail
- Navigate to Guardrails → Create
- Search for “Detect PII” under PRO guardrails
- Select PII categories to detect:
- Phone Numbers: Mobile and landline numbers
- Email Addresses: Personal and corporate emails
- Location Information: Addresses, cities, coordinates
- IP Addresses: IPv4 and IPv6 addresses
- Social Security Numbers: US SSN format
- Names: First names, last names, full names
- Credit Card Information: Card numbers
Step 2: Enable PII Redaction
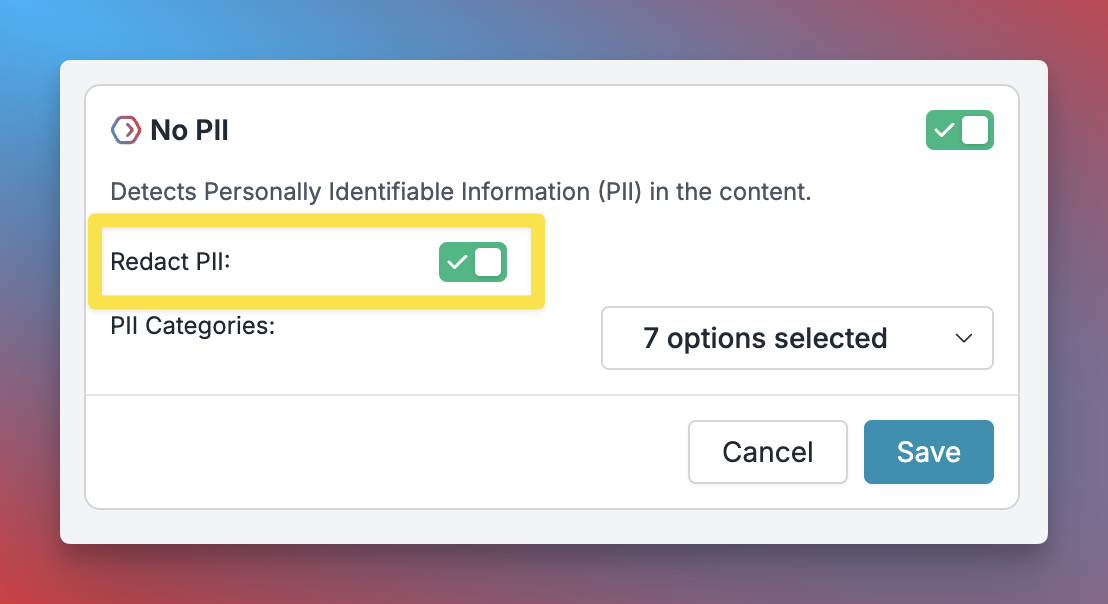
Step 3: Configure Guardrail Actions
Set up how your guardrail should behave:- Async: Run checks without blocking (default: TRUE)
- Deny: Block requests with PII (default: FALSE)
- On Success/Failure: Send feedback for monitoring
Step 4: Add to Config and Use
Once you save your guardrail, you’ll get a Guardrail ID. Add it to your config:The examples below demonstrate input guardrails only. You can also apply PII detection to outputs by adding guardrails to
output_guardrails.Real-World Examples: Portkey vs Bedrock
Let’s see how Portkey and AWS Bedrock handle the same PII-containing requests:- Python Setup
- Node.js Setup
Email Address Detection
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:What Portkey Detected:
EMAIL_ADDRESS_1: john.doe@example.comEMAIL_ADDRESS_2: john.smith@company.com
Phone Number Detection
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:What Portkey Detected:
PHONE_NUMBER_1: (555) 123-4567PHONE_NUMBER_2: +1-800-555-0123
Social Security Number Protection
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:What Portkey Detected:
SSN_1: 123-45-6789
Credit Card Information
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:What Portkey Detected:
CREDIT_CARD_1: 4532CREDIT_CARD_2: 4532-1234-5678-9012
Name Detection
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:What Portkey Detected:
NAME_1: John SmithNAME_2: Jane Doe
Address Detection
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:What Portkey Detected:
LOCATION_ADDRESS_1: 123 Main Street, Apt 4B, New York, NY 10001
IP Address Detection
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:What Portkey Detected:
IP_ADDRESS_1: 192.168.1.100IP_ADDRESS_2: 10.0.0.1
Complex Real-World Scenarios
Financial Services Example
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:Detected PII:
- Individual tracking with numbered placeholders
- Account number not redacted (customize if needed)
Legal Document Example
Original Query:- Portkey Result
- Bedrock Result
Transformed Input:Unique Tracking: Each instance tracked separately
Key Differences: Portkey vs Bedrock
| Feature | Portkey Native | AWS Bedrock |
|---|---|---|
| Placeholder Style | Numbered (e.g., [NAME_1], [NAME_2]) | Generic (e.g., {NAME}) |
| Instance Tracking | ✅ Each PII instance tracked separately | ✅ Same placeholder for same type |
| Names | [NAME_X] | {NAME} |
| Emails | [EMAIL_ADDRESS_X] | {EMAIL} |
| Phone Numbers | [PHONE_NUMBER_X] | {PHONE} |
| SSN | [SSN_X] | {US_SOCIAL_SECURITY_NUMBER}{SSN_REGEX} |
| Addresses | [LOCATION_ADDRESS_X] | {ADDRESS} |
| Credit Cards | [CREDIT_CARD_X] | {CREDIT_DEBIT_CARD_NUMBER} |
| IP Addresses | [IP_ADDRESS_X] | {IP_ADDRESS} |
| Bank Accounts | Not in default categories | {US_BANK_ACCOUNT_NUMBER} |
When to Use Which?
Choose Portkey Native PII Detection when:- You need to track individual PII instances
- You want numbered placeholders for better context
- You prefer simple, consistent placeholder format
- You need quick setup without AWS configuration
- You’re already using AWS infrastructure
- You need specific US-format detection (US_BANK_ACCOUNT_NUMBER)
- You want dual detection patterns (e.g., SSN + regex)
- You need to comply with AWS security standards
Monitoring PII Detection
Viewing Results in Portkey Logs
Navigate to your Portkey logs to see:
- Original Request: What the user sent
- Final (Transformed): What was sent to the LLM
- Guardrail Status: Shows if PII detection succeeded
- Detected Entities: List of all PII found
Understanding Response Codes
- 200: Request successful (PII redacted if found)
- 246: PII detected but request continued (Deny = false)
- 446: Request blocked due to PII (Deny = true)

