Enabling PII Redaction
On the Guardrail creation page, for select PII guardrails, you will see a Redact PII toggle. Just enable it to start redacting PII in your requests.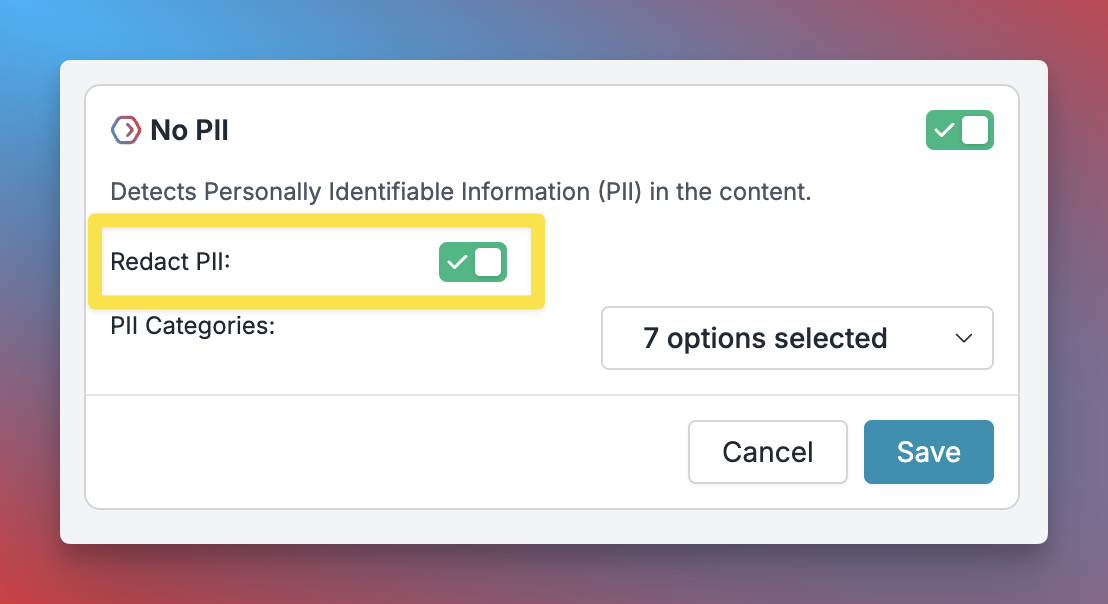
Guardrails Support
PII redaction is supported across 5 guardrail providers:Portkey Pro PII
Redact
Phone number, Email addresses, Location information, IP addresses, Social Security Numbers (SSN), Names, Credit card information from requestsPatronus AI
Based on Patronus’s EnterprisePII dataset, this guardrail can detect and redact confidential information typically found in business documents like meeting notes, commercial contracts, marketing emails, performance reviews, and more
Pangea
Pangea’s redact feature can redact PII like geographic locations, payment card industry (PCI) data, and many other types of sensitive information, with support for rule customization
AWS Bedrock Guardrails
You can select from a list of predefined PII or define a custom sensitive-information type using regular expressions (RegEx) and redact PII.
Promptfoo
Promptfoo helps detect multiple PII exposures - in session data, via social engineering, or a direct exposure.
Custom PII Redaction with Regex
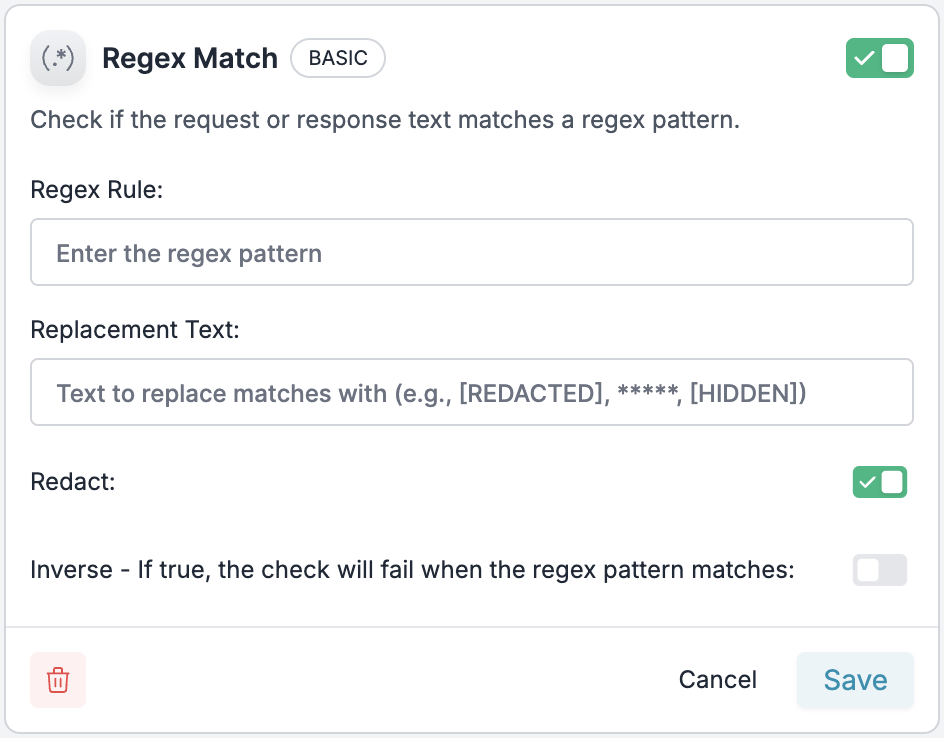
For more granular control over PII redaction, you can create custom patterns using Portkey’s Regex Match guardrail with redaction capabilities. This allows you to define specific patterns for sensitive information unique to your use case.Setting Up Custom PII Patterns
-
Navigate to Guardrails: Go to the
Guardrailspage and clickCreate - Select Regex Match: Choose the “Regex Match” guardrail from the BASIC category
-
Configure the Pattern:
- Regex Rule: Enter your regex pattern to match specific PII (e.g.,
\b\d{3}-\d{2}-\d{4}\bfor SSN patterns) - Replacement Text: Define what to replace matches with (e.g.,
[REDACTED],*****,[SSN_HIDDEN]) - Enable Redact: Toggle the “Redact” option to
ON - Inverse: Keep this
OFFunless you want to redact everything except the pattern
- Regex Rule: Enter your regex pattern to match specific PII (e.g.,
- Save the Guardrail: Name your guardrail and save it to get the associated Guardrail ID
Common Regex Patterns for PII
Adding to Your Config
Once you’ve created your custom PII regex guardrail, add it to your Portkey config:You can add the same guardrail to both
before_request_hooks (input guardrails) and after_request_hooks (output guardrails) to scan and redact PII in both user inputs and LLM responses.Example Implementation
- NodeJS
- Python
How It Works
- Detection: When enabled, the system scans incoming or outgoing requests for PII using the configured guardrail provider.
-
Redaction: Detected PII is automatically replaced with standardized identifiers:
- Email addresses →
{{EMAIL_ADDRESS_1}},{{EMAIL_ADDRESS_2}}, etc. - Phone numbers →
{{PHONE_NUMBER_1}},{{PHONE_NUMBER_2}}, etc. - And similar patterns for other PII types
- Email addresses →
- Processing: The redacted request is then forwarded to the LLM, ensuring sensitive data never reaches the model.
Monitoring PII Redaction
You can track request transformations through two key indicators in the request/response body:transformedboolean flag: Indicates whether any redaction occurredcheck_resultsobject: Contains detailed information about specific transformations
Best Practices
-
Gradual Implementation:
- Start by enabling the feature for a subset of requests
- Monitor the logs and transformation results
- Gradually expand coverage after validation
-
Regular Monitoring:
- Review transformation logs periodically
- Validate that sensitive information is being caught appropriately
-
Documentation:
- Maintain records of what types of PII you’re scanning for
- Document any specific compliance requirements being addressed
Security Considerations
- Redaction is irreversible by design
- Original PII storage and handling varies by guardrail provider
- The feature can be applied to both input and output content
- Custom regex patterns should be carefully designed to avoid false positives
- Preventing accidental exposure of sensitive data to LLMs
- Providing audit trails of PII handling
- Supporting data minimization principles
- Enabling systematic PII management across AI operations
Limitations
- Redaction patterns are not customizable for pre-built guardrails (but can be customized using regex)
- Transformation is one-way (non-reversible)
- Performance may vary based on chosen guardrail provider
- Complex regex patterns may impact processing latency
Troubleshooting
If you experience issues:- Verify the feature is enabled in your guardrails configuration
- Check the
transformedflag andcheck_resultsfor specific transformation details - Review logs for any error messages or unexpected behavior
- For custom regex patterns, validate the regex syntax and test with sample data
- Contact us here for additional assistance
FAQs
Can I customize the redaction patterns?
Can I customize the redaction patterns?
Currently, redaction patterns are standardized and not customizable.
How does the system handle multiple instances of the same type of PII?
How does the system handle multiple instances of the same type of PII?
Each instance receives a numbered identifier (e.g.,
{{EMAIL_ADDRESS_1}}, {{EMAIL_ADDRESS_2}}, etc.).Does this feature impact request latency?
Does this feature impact request latency?
Impact varies by guardrail provider and request complexity. Custom regex patterns with complex expressions may add minimal latency.
Can I use this feature with any LLM?
Can I use this feature with any LLM?
Yes, the feature works with any LLM supported by Portkey.
Does this feature work on both input and output?
Does this feature work on both input and output?
Yes, you can configure the guardrail to scan both requests and responses.
Can I combine multiple PII redaction methods?
Can I combine multiple PII redaction methods?
Yes, you can use multiple guardrails in the same config to combine pre-built PII detection with custom regex patterns.

